Courtesy - Imperva
The COVID-19 pandemic drastically disrupted work life worldwide. Almost overnight, the percentage of employees working remotely grew exponentially and fundamentally shifted where and when employees work and how they gain access to company networks.
Microsoft’s Work Trend Index 2022 found that hybrid work is up to 38% and that 53% of people are likely to consider transitioning to hybrid in the year ahead. Those figures align with the digital trend that’s evolved over the last decade, making it easier for individuals to collaborate across offices and remote locations. This increase in remote and hybrid work has led to growing concern about insider risk incidents, where-in data theft or data destruction from departing employees is a form of insider risk that is becoming more commonplace.
A 2022 cost of insider threat survey by Ponemon Institute found that insider-led cybersecurity incidents have increased by 44% over the last two years, with average annual costs of known insider-led incidents up more than a third to $15.38 million.
What is insider risk?
Insider risk is defined as the potential for a person to use authorized access to the organization’s assets—either maliciously or unintentionally—in a way that negatively affects the organization. Access includes both physical and virtual (cyber) access; assets include information, processes, systems, and facilities.
What is insider risk management?
Activities intended to detect, prevent and recover from an incident involving a person using authorized access to the organization’s assets—either maliciously or unintentionally—in a way that negatively affects the organization. These activities can be performed in a formally coordinated manner, as part of a centralized program, or more informally outside of an organized program or structure is defined as insider risk management.
What are common types of insider risk?
There are two main categories of insider risk that we focus on: inadvertent and malicious. While malicious cases— including fraud, IP theft, and even corporate espionage—are perhaps what first come to mind when the topic of insider risk arises, inadvertent cases—which can include an employee unknowingly taking unsafe actions—are more common by far. Malicious cases, while less common, can be more costly.
Inadvertent (Accidental)
An employee unintentionally causes harm. This can occur when an employee:
- Takes unsafe actions
- Is untrained or distracted
- Misuses resources
- Causes other accidental data leakage, loss or destruction
Malicious
An employee sets out to cause harm, such as:
- Fraud
- IP theft
- Unauthorized disclosure
- Corporate espionage
- Sabotage & destruction
How to recover from Accidental or Malicious data destruction?
Identify all your applications which contain critical data and have a SaaS backup strategy for that data. Not only should you have a data backup strategy in place, you should frequently test the recovery processes of the system to ensure things are working to your requirements.
How can Revyz help?
Trusted by more than 100,000 organizations, Atlassian’s Jira Software is a powerful work management tool for all kinds of use cases, from requirements and test case management to agile software development. Revyz helps protect your Jira Software data by automatically backing up all the data into secure offsite location and enables for an on-demand granular recovery of the data. The Jira backup & restore solution offered by Revyz helps customers protect their Jira data from the below listed insider and outsider risk’s.
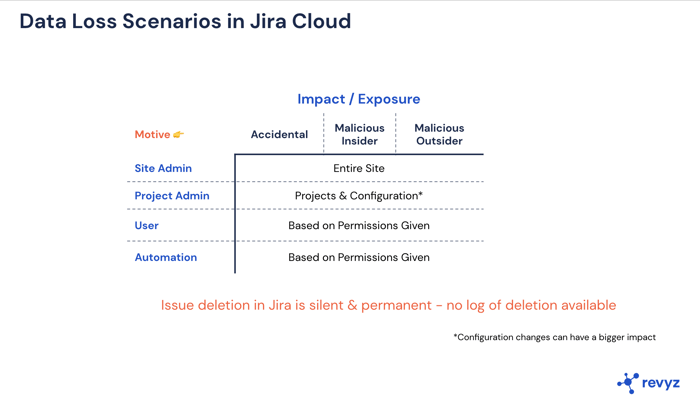 Issue deletion in Jira is silent & permanent - no log of deletion available, Configuration changes can have a bigger impact. Learn more on the capabilities of the Revyz offering here.
Issue deletion in Jira is silent & permanent - no log of deletion available, Configuration changes can have a bigger impact. Learn more on the capabilities of the Revyz offering here.
Blogs from Revyz
Atlassian Data Protection - Challenges in the Cloud
7 Reasons Why A Jira Backup & Restore Solution Is A Must Have
Pro’s and Con’s of using Jira Cloud Database Backup & Restore
Mystery of Incorrect Sprint Reports
Jira - Restoring Issue Family Hierarchy
SaaS Backup: An Antidote to Ransomware
Data Backup - A Key Pillar of Insider Risk Management
What’s your Atlassian Cloud Migration & Data Protection Strategy?
A Guide to SaaS Shared Responsibility Model

